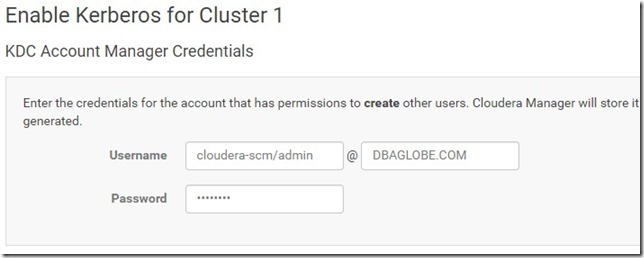
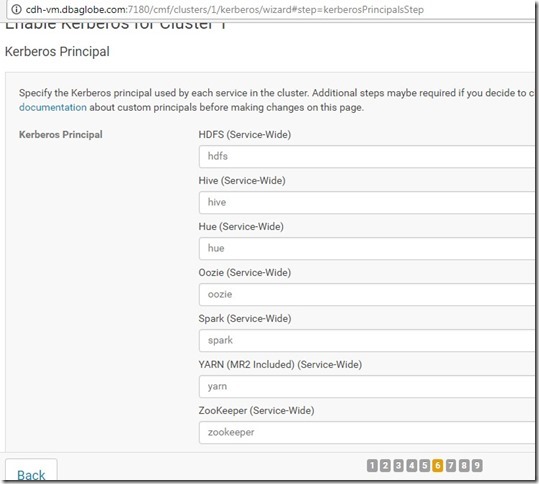
- Create keberos admin user who has privivleges to to add other principals
[root@cdh-vm krb5kdc]# kadmin.local -q "addprinc cloudera-scm/admin"
-- Before proceed, verify the KDC works:
ktutil: add_entry -password -p cloudera-scm/admin -k 1 -e aes256-cts-hmac-sha1-96
Password for cloudera-scm/admin@DBAGLOBE.COM:
[root@cdh-vm log]# klist -e
Ticket cache: KEYRING:persistent:0:krb_ccache_r0tnzhY
Default principal: cloudera-scm/admin@DBAGLOBE.COM
Valid starting Expires Service principal
11/09/2017 23:09:42 11/10/2017 23:09:42 krbtgt/DBAGLOBE.COM@DBAGLOBE.COM
Etype (skey, tkt): aes256-cts-hmac-sha1-96, aes256-cts-hmac-sha1-96
| Encountered errors: 2017-11-09 23:34:18,010 INFO org.apache.hadoop.ipc.Server: Socket Reader #1 for port 8022: readAndProcess from client 192.168.56.10 threw exception [javax.security.sasl.SaslException: GSS initiate failed [Caused by GSSException: Failure unspecified at GSS-API level (Mechanism level: Encryption type AES256 CTS mode with HMAC SHA1-96 is not supported/enabled)]] How to Fix: [root@cdh-vm security]# pwd [root@cdh-vm security]# mkdir limited |




No comments:
Post a Comment